Fine-grained access control in API Gateway with Cognito access token and scopes
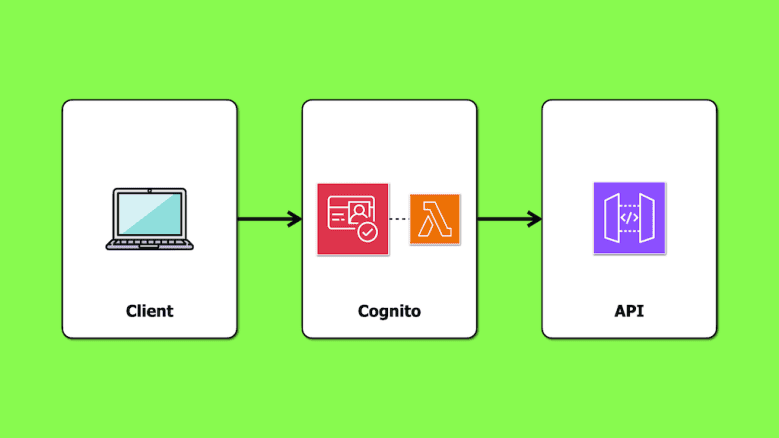
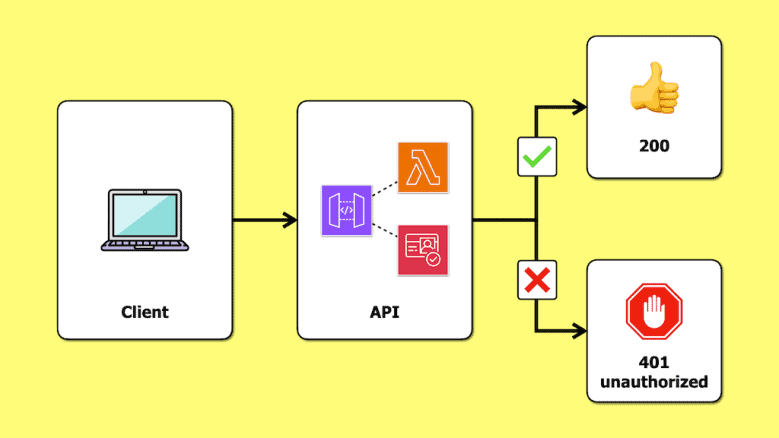
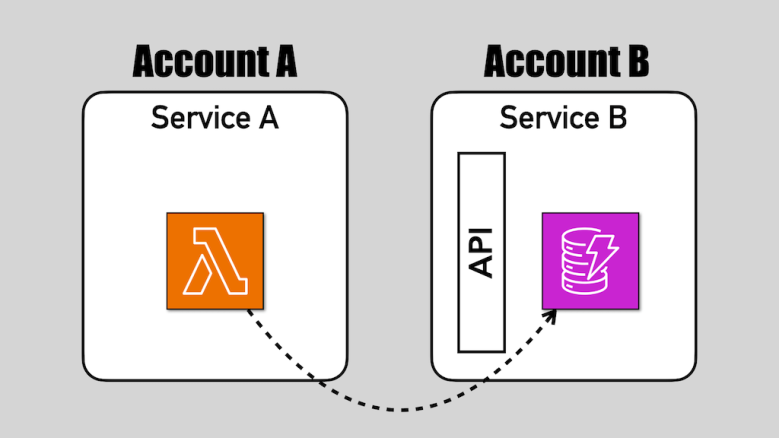
In this post, we look at how you can implement fine-grained access control using Cognito access tokens and scopes. We will discuss the trade-offs of this approach and the cost implications of enabling Cognito’s Advanced Security Features (required for this approach to work).
Personally, I think this is too costly an approach and doesn’t offer enough upside in return.
Unless you’re using Advanced Security Features already, or your application has a high value per user (e.g. a B2B enterprise application), this approach may be difficult to justify in terms of return on investment.