
Yan Cui
I help clients go faster for less using serverless technologies.
This article is brought to you by

The real-time data platform that empowers developers to build innovative products faster and more reliably than ever before.
Disclaimer: if you’re new to CloudFormation custom resources, then I recommend you start by reading this excellent post by Alex Debrie first.
Custom resources bring a whole new dimension to CloudFormation and enable some fascinating use cases. For example:
- provision DataDog dashboards as part of your CloudFormation stack
- run a load test every time you deploy a CloudFormation stack
- provision/modify AWS resources that are not natively supported by CloudFormation (e.g. EventBridge)
You can use custom resources to run one-off tasks as part of every CloudFormation deployment. Which is something I wanted to do in many of my SAR apps such as this and this. However, I had always assumed that this would require a two-step process:
- deploy a SAR/CloudFormation stack to provision the custom resource Lambda function
- deploy the intended SAR app which uses the custom resource
Turns out, I was wrong. You can include the custom resource Lambda function in the same CloudFormation stack that uses it. In hindsight, I was overthinking things – in essence, all we are doing is referencing a Lambda function by ARN. You’ll see what this means later.
My latest SAR app, propagate-cfn-tags, tackles the issue that CloudFormation does not propagate its tags to some resources such as CloudWatch log groups. This means you can’t include CloudWatch log groups in your cost monitoring (via cost allocation tags), amongst other things.
When you deploy the app, I want to run a one-off script to process all existing stacks in the region and propagate their tags. This is where custom resources come in.
With the help of custom resources, I can:
- create a
PropagateAllLambda function to process existing CloudFormation stacks
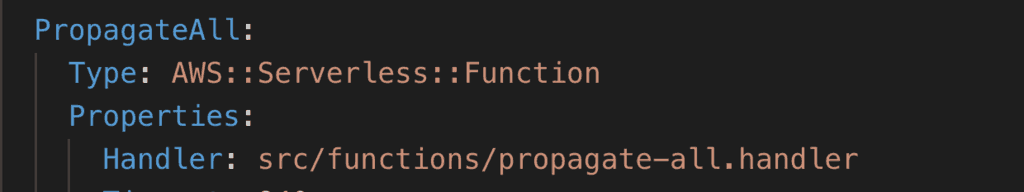
- create a Lambda function to support a
Custom::LambdaInvocationcustom resource type
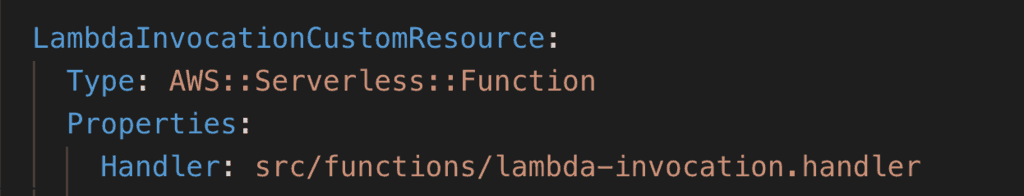
- create a
Custom::LambdaInvocationresource to trigger thePropagateAllfunction during the CloudFormation deployment
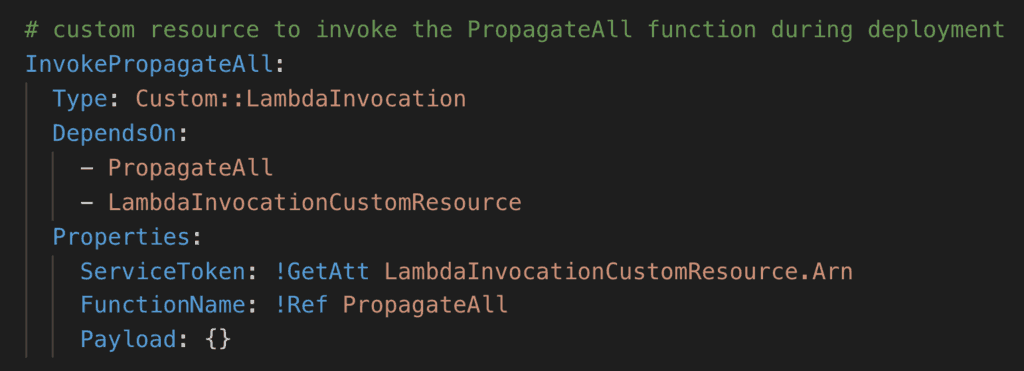
I can do all these in the same SAR app. This gives the user a seamless experience. As far as they’re concerned, you just deploy the app and everything happens as advertised. No two-step deployment process, no need to trigger functions manually.
This simple pattern combines very well with CloudWatch events (or EventBridge):
- a custom resource to update existing resources (e.g. propagate tags for existing CloudFormation stacks)
- CloudTrail + event pattern to process future changes (e.g. propagate tags for future CloudFormation stack deployments)
I find this combination especially useful when building “platform” features. That is, features that span across all my applications running in AWS. For example, making sure all CloudWatch log groups are subscribed to a Kinesis stream. These are not decision points that should be taken at the project level. Which is why I’m not a fan of using Serverless framework plugins to configure these settings.
Whenever you’re ready, here are 4 ways I can help you:
- Production-Ready Serverless: Join 20+ AWS Heroes & Community Builders and 1000+ other students in levelling up your serverless game. This is your one-stop shop for quickly levelling up your serverless skills.
- Do you want to know how to test serverless architectures with a fast dev & test loop? Check out my latest course, Testing Serverless Architectures and learn the smart way to test serverless.
- I help clients launch product ideas, improve their development processes and upskill their teams. If you’d like to work together, then let’s get in touch.
- Join my community on Discord, ask questions, and join the discussion on all things AWS and Serverless.