
Yan Cui
I help clients go faster for less using serverless technologies.
In a previous post we discussed how to auto-subscribe a CloudWatch Log Group to a Lambda function using CloudWatch Events. So that we don’t need a manual process to ensure all Lambda logs would go to our log aggregation service.
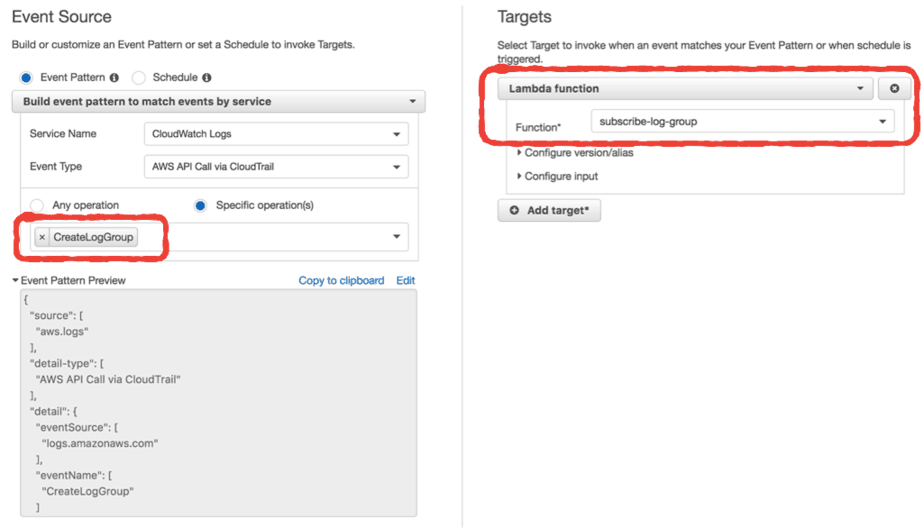
Whilst this is useful in its own right, it only scratches the surface of what we can do. CloudTrail and CloudWatch Events makes it easy to automate many day-to-day operational steps. With the help of Lambda of course ;-)
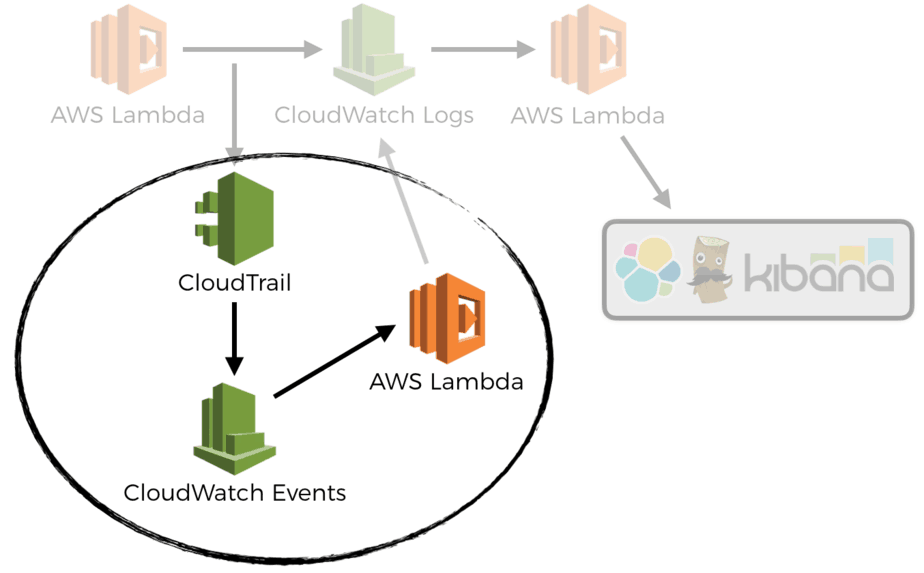
I work with API Gateway and Lambda heavily. Whenever you create a new API, or make changes, there are several things you need to do:
- enable Detailed Metrics for the deployment stage
- set up a dashboard in CloudWatch, showing request count, latencies and error counts
- set up CloudWatch Alarms for p99 latencies and error counts
Because these are manual steps, they often get missed.
Have you ever forgotten to update the dashboard after adding a new endpoint to your API? And did you also remember to set up a p99 latency alarm on this new endpoint? How about alarms on the no. of 4XX or 5xx errors?
Most teams I have dealt with have some conventions around these, but without a way to enforce them. The result is that the convention is applied in patches and cannot be relied upon. I find this approach doesn’t scale with the size of the team.
It works when you’re a small team. Everyone has a shared understanding, and the necessary discipline to follow the convention. When the team gets bigger, you need automation to help enforce these conventions.
Fortunately, we can automate away these manual steps using the same pattern. In the Monitoring unit of my course Production-Ready Serverless, I demonstrated how you can do this in 3 simple steps:
- CloudTrail captures the CreateDeployment request to API Gateway.
- CloudWatch Events pattern against this captured request.
- Lambda function to a) enable detailed metrics, and b) create alarms for each endpoint
If you use the Serverless framework, then you might have a function that looks like this:
auto-create-api-alarms:
handler: functions/create-alarms.handler
events:
- cloudwatchEvent:
event:
source:
- aws.apigateway
detail-type:
- AWS API Call via CloudTrail
detail:
eventSource:
- apigateway.amazonaws.com
eventName:
- CreateDeployment
environment:
alarm_actions: arn:aws:sns:#{AWS::Region}:#{AWS::AccountId}:NotifyMe
ok_actions: arn:aws:sns:#{AWS::Region}:#{AWS::AccountId}:NotifyMe
iamRoleStatements:
- Effect: Allow
Action: apigateway:GET
Resource:
- arn:aws:apigateway:#{AWS::Region}::/restapis/*
- arn:aws:apigateway:#{AWS::Region}::/restapis/*/stages/${self:custom.stage}
- Effect: Allow
Action: apigateway:PATCH
Resource: arn:aws:apigateway:#{AWS::Region}::/restapis/*/stages/${self:custom.stage}
- Effect: Allow
Action: cloudwatch:PutMetricAlarm
Resource: "*"
Couple of things to note from the code above:
- I’m using the serverless-iam-roles-per-function plugin to give the function a tailored IAM role
- The function needs the
apigateway:PATCHpermission to enable detailed metrics - The function needs the
apigateway:GETpermission to get the API name and REST endpoints - The function needs the
cloudwatch:PutMetricAlarmpermission to create the alarms - The environment variables specify SNS topics for the CloudWatch Alarms
The captured event looks like this:
{
"version": "0",
"id": "dee9a69c-8166-1ad7-41d4-1dad201e29f6",
"detail-type": "AWS API Call via CloudTrail",
"source": "aws.apigateway",
"account": "374852340821",
"time": "2018-04-09T00:17:47Z",
"region": "us-east-1",
"resources": [],
"detail": {
"eventVersion": "1.05",
"userIdentity": {
"type": "IAMUser",
"principalId": "AIDAIRMUZZEGPO27IPFYW",
"arn": "arn:aws:iam::374852340821:user/yan.cui",
"accountId": "374852340821",
"accessKeyId": "ASIAJNZDKN26DXPZFYQE",
"userName": "yan.cui",
"sessionContext": {
"attributes": {
"mfaAuthenticated": "false",
"creationDate": "2018-04-09T00:17:30Z"
}
},
"invokedBy": "cloudformation.amazonaws.com"
},
"eventTime": "2018-04-09T00:17:47Z",
"eventSource": "apigateway.amazonaws.com",
"eventName": "CreateDeployment",
"awsRegion": "us-east-1",
"sourceIPAddress": "cloudformation.amazonaws.com",
"userAgent": "cloudformation.amazonaws.com",
"requestParameters": {
"restApiId": "8kbasri6v7",
"createDeploymentInput": {
"stageName": "dev"
},
"template": false
},
"responseElements": {
"id": "cj2y0f",
"createdDate": "Apr 9, 2018 12:17:47 AM",
"deploymentUpdate": {
"restApiId": "8kbasri6v7",
"deploymentId": "cj2y0f",
"template": false
},
"deploymentStages": {
"deploymentId": "cj2y0f",
"restApiId": "8kbasri6v7",
"template": false,
"templateSkipList": [
"position"
]
},
"deploymentDelete": {
"deploymentId": "cj2y0f",
"restApiId": "8kbasri6v7",
"template": false
},
"self": {
"deploymentId": "cj2y0f",
"restApiId": "8kbasri6v7",
"template": false
}
},
"requestID": "6e25bd56-3b8b-11e8-a351-e5e3d3161fe7",
"eventID": "a150d941-7a54-4572-97b2-0614a81fd25b",
"readOnly": false,
"eventType": "AwsApiCall"
}
}
We can find the restApiId and stageName inside the detail.requestParameters attribute. That’s all we need to figure out what endpoints are there, and so what alarms we need to create.
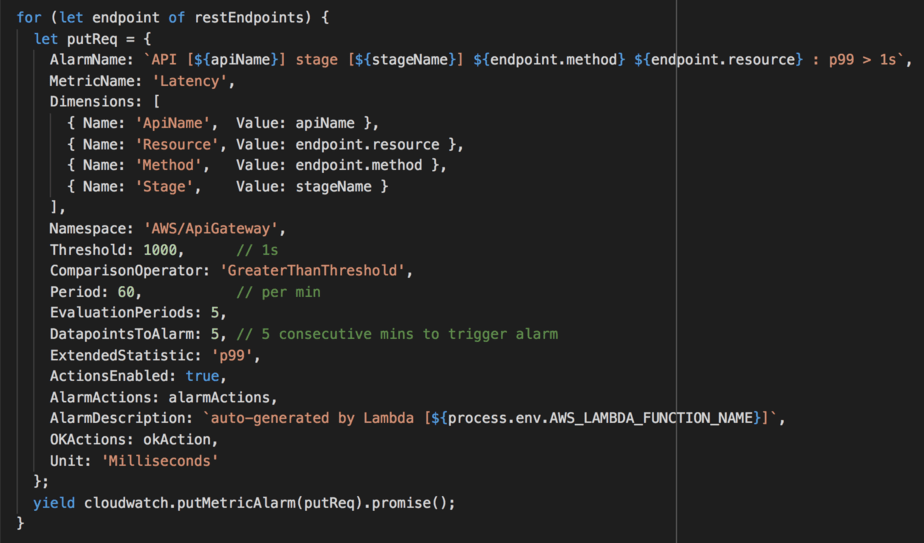
Inside the handler function, which you can find here, we perform a few steps:
- enable detailed metrics with an
updateStagecall to API Gateway - get the list of REST endpoints with a
getResourcescall to API Gateway - get the REST API name with a
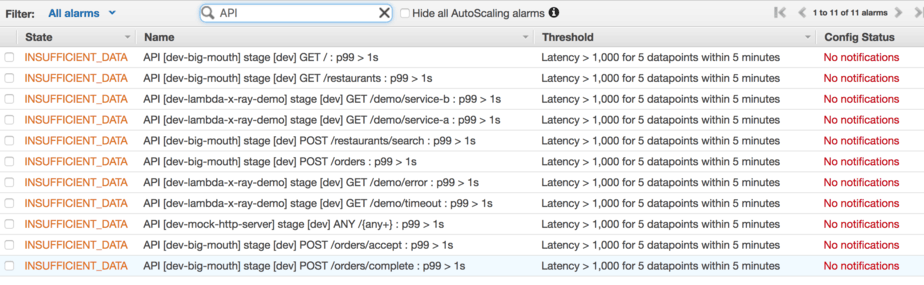
getRestApicall to API Gateway - for each of the REST endpoints, create a p99 latency alarm in the
AWS/ApiGatewaynamespace
-
create CloudWatch Alarms for 5xx errors for each endpoint
-
create CloudWatch Dashboard for the API
So there you have it, a useful pattern for automating away manual ops tasks!
Whenever you’re ready, here are 3 ways I can help you:
- Production-Ready Serverless: Join 20+ AWS Heroes & Community Builders and 1000+ other students in levelling up your serverless game. This is your one-stop shop for quickly levelling up your serverless skills.
- I help clients launch product ideas, improve their development processes and upskill their teams. If you’d like to work together, then let’s get in touch.
- Join my community on Discord, ask questions, and join the discussion on all things AWS and Serverless.
